ICT318 Network security Tutor-Marked Assignment (TMA) July 2025 Presentation

Question 1 (25 marks)
(a) To apply a block cipher in applications, a few modes of operation. One such mode of operation is the Cipher Block Chaining Mode (CBC). Discuss what is block cipher and how this mode of operation works. What could be one of the issues related to this mode of operation?(6 marks)
(b) Sometimes, one may need authenticity of a message but not necessarily confidentiality of message. Explain your answer clearly by giving a concrete application scenario.(5 marks)
(c) In Activity 3 of Study Unit 1, Chapter 1, download the X.800: Security Architecture for Open Systems Interconnection for CCITT applications publication. Go through the publication and attempt to answer the following questions:
- What do you understand by ‘notarization’ and discuss how does it work? (4 marks)
- What are the two forms of non-repudiation and determine the relationship between non-repudiation and notarization?(4 marks)
- Identify TWO (2) security services that are provided in layer 6 and layer 7 of the ISO seven layers and briefly discuss how these security services are provided over these layers.(6 marks)
Question 2 (25 marks)
(a)Examine the following message packet.

- Appraise how can one be reasonably sure that the message is authentic, if the message is encrypted.(6 marks)
- Assess whether it would be sufficient to just encrypt the actual data field, or the entire message needs to be encrypted and why?(3 marks)
(b)Apply asymmetric cryptosystem and hashing function, describe how they can be used to provide authentication and non-repudiation. Illustrate your answer with the aid of a diagram.(9 marks)
(c)The following resultant ciphertext, GLFSSDVARV was obtained using two symmetric algorithms (i.e. Caesar Cipher and Vernam Cipher) with the appropriate key given below:
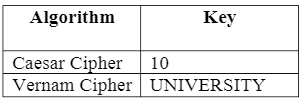
Verify clearly and determine the original plaintext, taking the value of the alphabet as: A= 0; B=1; C=2; etc. Please note that you need to show your full workings.(7 marks)
Do You Need ICT318 TMA Assignment of This Question
Order Non Plagiarized Assignment
Question 3 (25 marks)
(a) Illustrate how Kerberos protocol for communication between Aaron and Betty can be used to address the following:
- When Betty receives a ticket from Aaron, how does she know that it is genuine and that it came from Aaron?(3 marks)
- When Aaron receives a reply from Betty, how does he know that it came from Betty (and not a possible ‘replay’ message from Betty)?(2 marks)
- How can both know that the message is secure?(2 marks)
- What are the threats that Kerberos addresses?(3 marks)
(b) Examine the email header of your email (based on Activity 5 of Study Unit 3, Chapter2). Apart from Gmail, analyse the email header of any email services (like Yahoo, Hotmail, etc). {Note: if you do not have an account with these email services, please create one and correspond with your relatives and friends}
- Provide the steps of how the email header may be read from the chosen email service. (2 marks)
- Briefly explain the different MIME headers of your email.(6 marks)
- Part of the email header information, you will notice three ARC headers: ARC-Seal, ARC-Message-Signature and ARC-Authentication-Results. Determine what is ARC and the information contains in each of the headers.(7 marks)
You will need to submit a snapshot of your analysis (i.e. contents of your email header).
Question 4
(a) Refer to the following website: https://www.cloudshark.org/captures/a9718e5fdb28 to access the SSL test pcap file. Explore the first 5 lines of the SSL_test pcap file and determine the following: {Please note that SSL is synonymous to TLS}
- the client’s and server’s addresses.(2 marks)
- cipher suite is being used in the series of exchanges(1 mark)
- Provide the first 8-bytes of the encrypted pre-master key and explain why was the pre-master key encrypted?(2 marks)
- assess the significance and purpose of the ‘Encrypted Alert’ in this case. (3 marks)
(b) The CEO of an IT services company will be going on a overseas engagement for the next few months. As he still needs to review and approve some large projects on hand, he intends to work from the hotel while he is overseas. As such, he needs to access the project documents located in the Microsoft SharePoint server in the company’s central office in Singapore. As these are confidential documents, there is a need to ensure secure access.
You have been tasked to investigate this requirement and make a technical recommendation using IPSEC. It is important that the communications between the CEO and the SharePoint server be protected against eavesdroppers, especially competitors. Also, it is imperative that the data must not been tampered with while in transit. Traffic analysis is not a concern, and the SharePoint servers are accessed by remote employees regularly. Examine the following IPSEC implementation options below. Recommend the configuration that will protect the data in the above scenario and discuss the reasons for your choice.
In your answer, also highlight why the other three options that you have not chosen, are not suitable. (i)Implement ESP (Encryption & Authentication)/Tunnel Mode at the Gateways.
(ii)Implement AH/Tunnel Mode at the Gateway.
(iii)Implement ESP (Encryption & Authentication)/Transport Mode at the CEO’s machine.
(iv)Implement AH/Transport Mode at the CEO’s machine.(10 marks)
(c) Implement a demilitarized zone (DMZ) is common firewall topology that most organisations embarked on. Describe how DMZ can provide added security protection to networks.(7 marks)

